Event Log Monitoring
Detect Suspicious Activity Before It Becomes a Threat
Monitor Event Logs for Signs of Potential Threats
Enterprotect 360 continually monitors the event logs of your Windows, Linux and MacOS devices, detecting and alerting you of suspicious activity.
Early Detection & ResponseStay one step ahead of cyber threats with Enterprotect 360. Event Log Monitoring continuously monitors your endpoints for suspicious activity, allowing you to respond quickly and prevent potential security threats. |
|
|
Unified Monitoring Across OS PlatformsMonitor all your endpoint event logs (Windows, Mac and Linux) through a single platform, eliminating the need for multiple tools, saving you time and effort while ensuring threat detection across all platforms. |
||||
Part of a Multi-Layered Security SystemEvent Log Monitoring is part of our multi-layered security system that provides 11 integrated layers of defence against more than 30 types of threats. |
77% of Small and Medium Sized Businesses Only Review Endpoint Event Logs After an Incident Occurs
77%
Endpoint Event Log Monitoring is critical in detecting potential security threats early so they can be prevented.
Hackers and malicious insiders can perform various actions on an endpoint that can go undetected by traditional security tools like firewalls and antivirus. For example, they may attempt to gain unauthorized access to sensitive data, install malware, or exploit vulnerabilities in the system. Once they gain a foothold on an endpoint, they can use it as a launching pad for lateral movement, moving laterally across the network to access other endpoints and systems. These actions can be performed stealthily and may not trigger alerts or notifications from traditional security tools.
Detecting and remediating potential cybersecurity threats early on can help prevent them from escalating into damaging cyberattacks, minimizing the impact on the organization and reducing the risk of financial and reputational harm.
Without proper log management, an organization can be blind to threats, malicious activity, and breaches. And, even worse, incidents that could have been prevented or responded to quickly may go undetected. - RSA Security
Centralized Event Log Storage
Enterprotect 360 securely stores monitored events, protecting them from tampering and providing easy access to event logs from any endpoint.
With Enterprotect 360 Event Log Monitoring, all monitored events are securely stored in a centralized location, protecting against attackers who may attempt to clear event logs to cover their tracks. The centralized storage ensures that event logs cannot be tampered with or lost due to local storage issues or device failures. In the event of a cyber attack, having centrally stored event logs can provide crucial evidence for identifying the root cause and scope of the attack, as well as aid in the recovery and remediation process.
Preconfigured & Easy to Use
You don’t need to be a security expert. Enterprotect 360 is preconfigured to monitor and analyze common security events on all platforms.
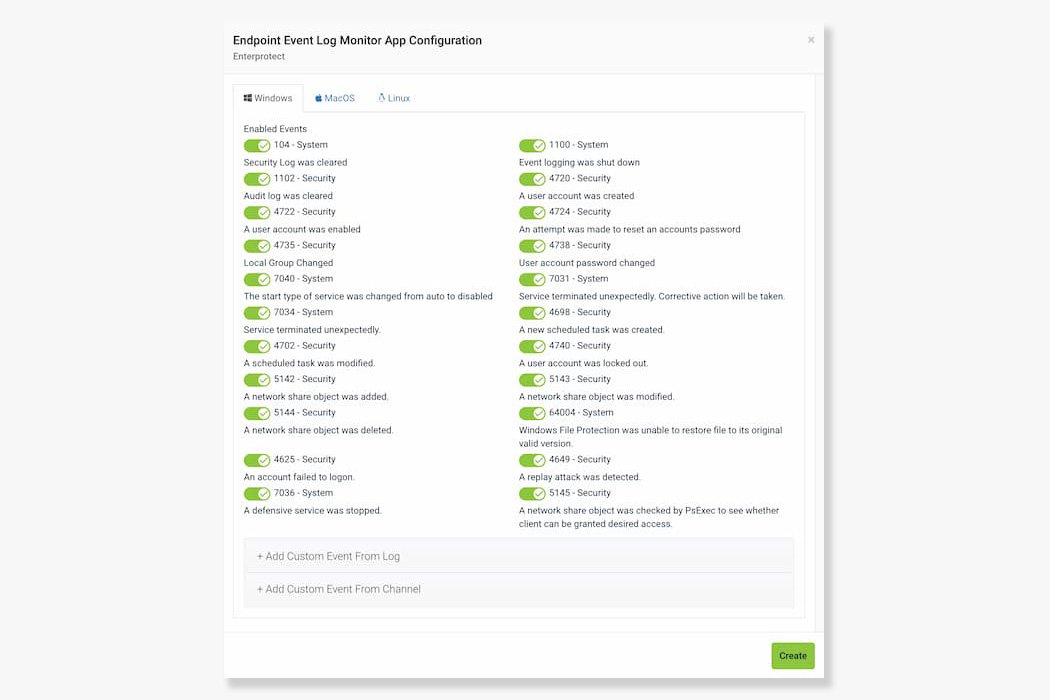
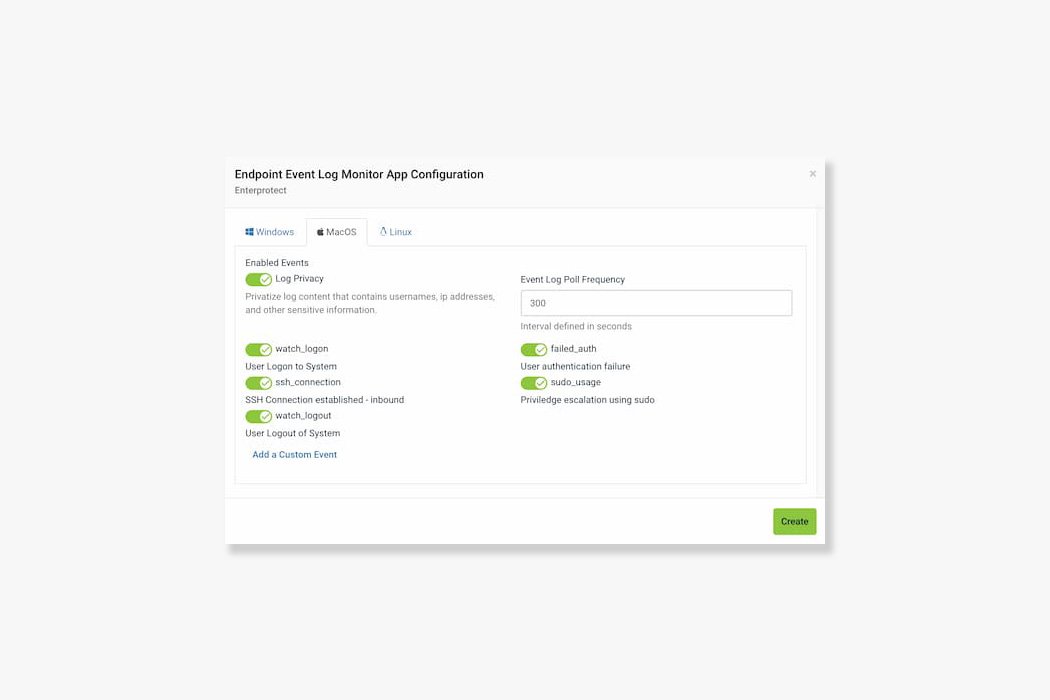
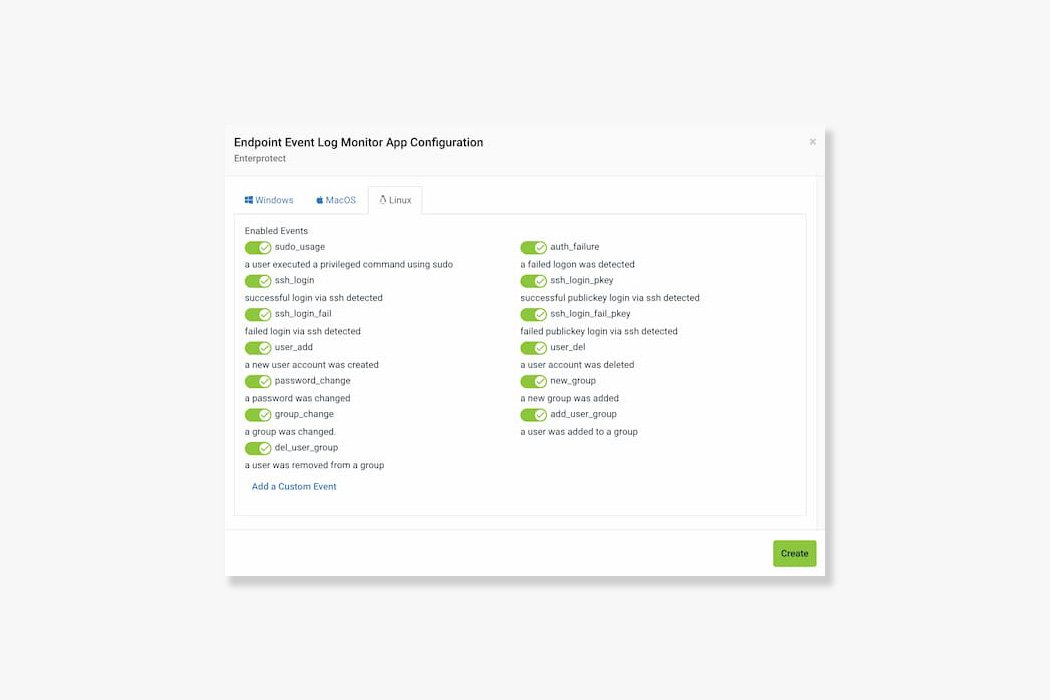
With Enterprotect 360 Event Log Monitoring, you have the flexibility to choose which event types you want to monitor for on each OS platform. This means that you can focus on the specific events that matter most to your organization's security, rather than getting bogged down with irrelevant data. In addition, you can create custom rules on all platforms, giving you even more control over what events are being monitored and how they are being analyzed. This customization allows you to tailor the monitoring to your unique needs and ensure that you are able to identify and respond to potential threats in a timely and effective manner.
Customizable Event Log Monitoring
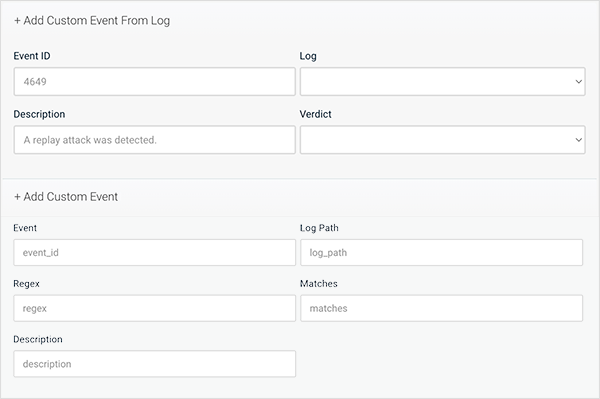
Do you have specific events you want to monitor? Or some you don’t? Setup custom event monitoring for each OS platform, tailored for your specific needs.
With Enterprotect 360 Event Log Monitoring, you have the flexibility to choose which event types you want to monitor for on each OS platform. This means that you can focus on the specific events that matter most to your organization's security, rather than getting bogged down with irrelevant data. In addition, you can create custom rules on all platforms, giving you even more control over what events are being monitored and how they are being analyzed. This customization allows you to tailor the monitoring to your unique needs and ensure that you are able to identify and respond to potential threats in a timely and effective manner.
Meet Compliance Requirements
Most Compliance standards require organizations to collect and store event logs. Enterprotect 360 Event Log Monitoring helps you meet these compliance requirements with ease.
Many organizations are required to store event logs for compliance purposes, as mandated by industry regulations and government laws. Compliance standards such as PCI-DSS, HIPAA, and GDPR require organizations to store and regularly review event logs for security incidents and to maintain a record of access to sensitive data. Storing event logs centrally in a secure location allows organizations to meet these requirements and provide auditors with the necessary evidence of compliance. Enterprotect 360 Event Log Monitoring provides a secure and centralized storage solution for endpoint event logs, helping organizations to comply with regulations and protect sensitive data.
Enterprotect 360 vs. SIEM
Traditional Security Information and Event Management (SIEM) solutions are powerful tools for collecting and analyzing logs from across an organization's IT infrastructure. However, they can be complex, expensive to deploy and maintain, and require a team of cybersecurity experts to operate effectively.
Enterprotect 360 takes a different approach, providing automated event log monitoring that is designed to be easy to use and accessible to IT teams of all sizes. Rather than overwhelming users with raw log data, Enterprotect 360 focuses on detecting and alerting on the security-related events that matter most.
Unlike many SIEMs and other log monitoring platforms, Enterprotect 360 is preconfigured with the most common security-related events for each OS platform, and allows users to easily create custom rules as needed. The Enterprotect 360 also supports cross-platform event log monitoring, eliminating the need for multiple tools and interfaces.
Keep Your Endpoints Secure Anywhere
Enterprotect 360's distributed architecture makes it an excellent solution for businesses with employees working remotely. This design enables Enterprotect 360 to monitor event logs on devices both on and off the network, ensuring that all endpoints are monitored regardless of their location. Whether employees are working in the office, at home, or on the road, Enterprotect 360 provides continuous monitoring and protection against potential threats.
Don't Let Suspicious Activity Go Unnoticed. Find and Investigate Them Now! Sign-up for a FREE TRIAL of Enterprotect 360.
Event Log Monitoring:
Just One Layer in our Multi-Layer Security Solution
ENTERPROTECT 360
Enterprotect 360 features 11 seamlessly integrated layers of protection, providing a robust defence against over 30 types of threats to ensure your organization's safety and security.
-
Enterprotect 360 continually scans the dark web for leaked passwords linked to your organization’s email addresses, enabling you to act on the data criminals are using to access your systems and network.
-
Enterprotect 360 continuously monitors your external-facing firewalls, servers, and applications for vulnerabilities - alerting you and providing guidance to quickly resolve vulnerabilities before they are exploited.
-
Enterprotect 360 blocks malicious domains to prevent your employees from being redirected to harmful websites and being subjected to malicious content — reducing their risk of falling victim to phishing, malware, ransomware, and zero-day threats.
-
Enterprotect 360 monitors your Microsoft 365 24/7 by ingesting logs, activities, alerts and Secure Score, detecting potential threats and risks. Experienced security experts promptly respond to suspicious activity, reducing attack dwell time.
-
Enterprotect 360 continually scans your environment for vulnerabilities and helps you quickly identify, prioritize and remediate flaws that could be exploited by hackers or malware.
-
Enterprotect 360 actively hunts for looks for footholds and backdoors on your organization's endpoints, such as suspicious or unauthorized tools, processes, services, or harmful files - alerting you to unusual activity that might indicate a compromise.
-
Enterprotect 360 helps protect your company from new and emerging threats by leveraging the latest threat intelligence to continuously monitor your computers for Indicators of Compromise, such as malicious IPs, domains, hashes, filenames, and other threat signatures.
-
Enterprotect 360 monitors the Event Logs of your Endpoints - alerting you of important security-related events, such as if a security log was cleared, a user account was enabled, an account failed to login or a replay attack was detected.
-
Enterprotect 360 monitors your computers for the tactics, techniques, and procedures TTPs used by hackers. By identifying suspicious behaviors early, we help you thwart attacks before they happen.
-
Enterprotect 360 harnesses the power of AI to rapidly detect, block, and automatically roll-back changes made by malware, such as viruses and ransomware.
-
Enterprotect 360 is monitored by experienced SOC analysts who provide around the clock eyes-on-glass monitoring and response to cyber incidents.
Sign-up for a free trial and try Enterprotect 360 free for 60 days!
Resources
Building a Business Case for Cybersecurity
A Guide for IT Professionals
As technology continues to play an increasingly important role in our lives, the need for cybersecurity has never been greater. This guide will provide you with the knowledge and tools you need to promote cybersecurity to leadership and increase investment in cybersecurity measures. By understanding the potential risks and costs of a cybersecurity breach and being able to present a clear and compelling case for increased investment, you'll be able to build a stronger, more secure organization.
Download the guide now and take the first step towards building a stronger, more secure organization.
Frequently Asked Questions
-
Event log monitoring is the process of monitoring and analyzing event logs generated by computer systems, applications, and network devices to detect potential security threats or suspicious activity.
-
Event log monitoring is important for cybersecurity because it enables organizations to detect and respond to potential threats early, reducing the risk of a damaging cyberattack. By analyzing event logs, organizations can identify patterns of suspicious activity and take proactive measures to protect their systems and data.
-
Enterprotect 360 monitors a variety of security-related events on Windows, MacOS, and Linux endpoints, including user authentication failures, password changes, new user accounts created, and more.
-
Enterprotect 360 is designed to simplify event log monitoring and analysis, providing a user-friendly interface and pre-configured rules to help organizations quickly identify potential threats. Unlike traditional SIEM solutions, Enterprotect 360 is easy to set up and requires minimal training.
-
Yes, Enterprotect 360 can monitor event logs on endpoints both on and off the network, providing comprehensive coverage of all endpoints and devices.
-
Enterprotect 360 continuously monitors event logs for potential threats, analyzing patterns of suspicious activity and alerting organizations when an anomaly is detected. By detecting threats early, organizations can take proactive measures to mitigate the risk of a damaging cyberattack.
-
Enterprotect 360 stores event logs in a secure, centralized location, protecting against tampering or loss due to local storage issues or device failures. The centralized storage ensures that event logs cannot be lost or altered, providing organizations with an auditable record of all endpoint activity.
-
Yes, Enterprotect 360 allows organizations to select which event types they want to monitor for on each OS platform, and create custom rules for more granular monitoring and analysis.
-
Enterprotect 360 helps organizations comply with industry regulations by providing a secure and centralized storage solution for endpoint event logs, which is required by many compliance standards. By automating event log monitoring and analysis, organizations can quickly identify potential threats and provide auditors with necessary evidence of compliance.
-
No, Enterprotect 360 is a cloud-based solution that does not require any additional hardware or software, making it easy to set up and use.
-
Event Log Monitoring is tightly integrated with other components of the Enterprotect 360 cybersecurity platform. Event Log Monitoring plays a critical role in Enterprotect 360’s Layered Approach to cybersecurity.
-
Enterprotect 360 is designed to be easy to set up and use, requiring minimal time and effort, simply install our agent. The solution is pre-configured to monitor the most common security-related events for each OS, and does not require extensive training or technical expertise.
-
Yes, Enterprotect 360 is designed to be scalable and flexible, making it suitable for organizations of all sizes and industries.
-
Enterprotect 360 simplifies event log monitoring and analysis, eliminating the need for manual log analysis and reducing the time and resources required to detect potential threats. The solution provides a centralized, user-friendly interface for monitoring event logs across multiple endpoints, streamlining the security monitoring process and freeing up IT resources for other critical tasks.
-
To get started with Event Log Monitoring, simply sign up for a free trial of Enterprotect 360, and install our agent. The agent begins collecting event logs immediately.